- Overview
- Transcript
3.13 Unvalidated Redirects
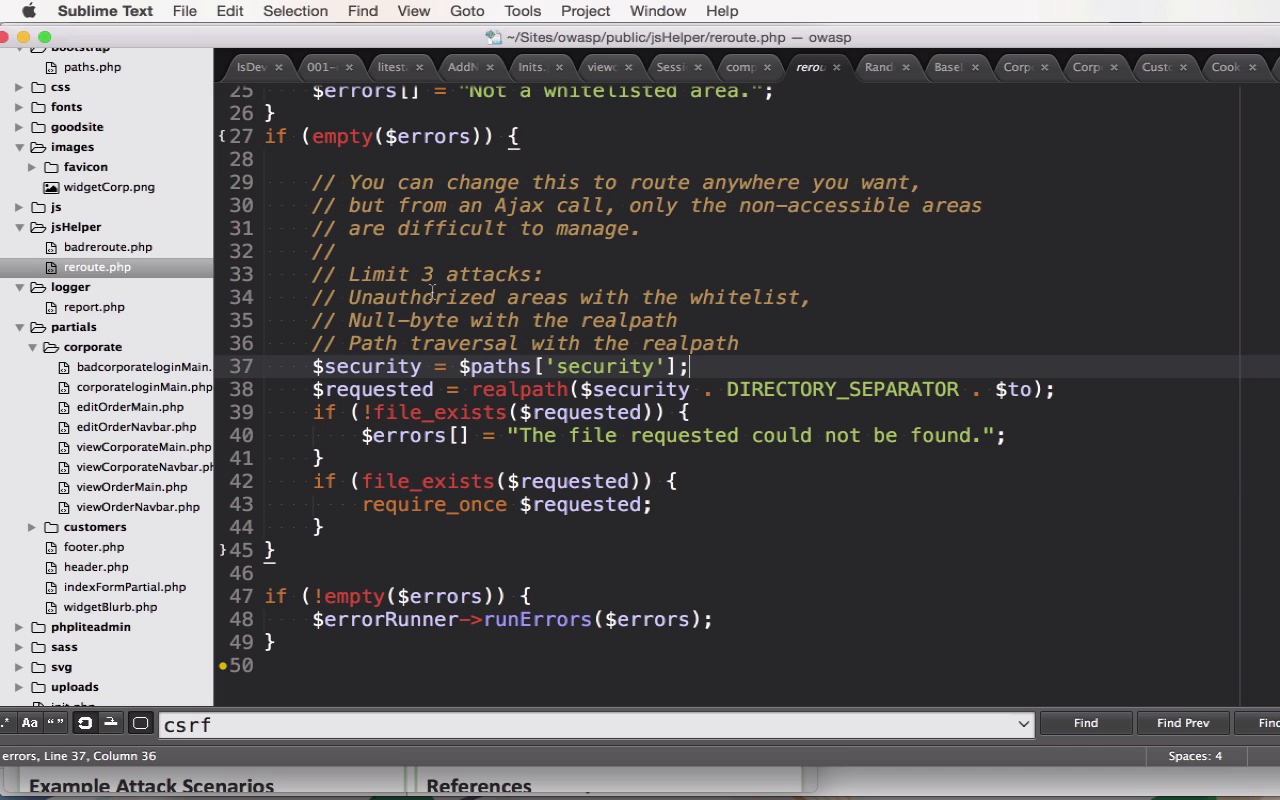
An unvalidated redirect occurs when a user follows a link that redirects them to another page, but where the redirect target can be modified by an attacker (e.g. when it is passed as a URL parameter). In this lesson, I'll show you a simple defense for unvalidated redirects. It involves whitelisting certain redirect targets and making sure that sanitation is performed on the redirect target URL to strip out relative paths and null-bytes.
1.Introduction1 lesson, 00:40
1 lesson, 00:40
1.1Introduction00:40
1.1
Introduction
00:40
2.The WidgetCorp App4 lessons, 34:39
4 lessons, 34:39
2.1Introducing the App10:09
2.1
Introducing the App
10:09
2.2Data Modeling04:19
2.2
Data Modeling
04:19
2.3Development Environment Setup10:32
2.3
Development Environment Setup
10:32
2.4Configuration Defaults09:39
2.4
Configuration Defaults
09:39
3.OWASP Top Ten14 lessons, 1:31:43
14 lessons, 1:31:43
3.1Injection Attacks and Defenses (Reflected, PHP, and JavaScript)07:38
3.1
Injection Attacks and Defenses (Reflected, PHP, and JavaScript)
07:38
3.2Injection Attacks (Mail, File, and SQL)05:16
3.2
Injection Attacks (Mail, File, and SQL)
05:16
3.3Injection Defenses (File System, Mail)15:04
3.3
Injection Defenses (File System, Mail)
15:04
3.4MySQL Injection Defenses02:46
3.4
MySQL Injection Defenses
02:46
3.5Authentication09:50
3.5
Authentication
09:50
3.6Broken Authentication and Session Management04:08
3.6
Broken Authentication and Session Management
04:08
3.7Insecure Direct Access or Object Reference05:20
3.7
Insecure Direct Access or Object Reference
05:20
3.8Security Configuration12:18
3.8
Security Configuration
12:18
3.9Sensitive Data08:26
3.9
Sensitive Data
08:26
3.10Missing Function-Level Access Control02:13
3.10
Missing Function-Level Access Control
02:13
3.11Cross-Site Request Forgery04:48
3.11
Cross-Site Request Forgery
04:48
3.12Known Vulnerable Components03:43
3.12
Known Vulnerable Components
03:43
3.13Unvalidated Redirects03:04
3.13
Unvalidated Redirects
03:04
3.14Brute-Force Attacks07:09
3.14
Brute-Force Attacks
07:09
4.Conclusion1 lesson, 00:48
1 lesson, 00:48
4.1Conclusion00:48
4.1
Conclusion
00:48
Michael Soileau started making websites with Ruby on Rails and WordPress and then moved onto full-stack development with LAMP, Node and front-end JavaScript. He also teaches web development and hosts meetups about web development in his spare time.